A Muddy, Advanced Persistent Teacher
16th November 2022
On 26th October 2022, the US Department of Treasury issued broad sanctions against Iranian entities including a cyber security company, Ravin Academy, and the two individuals that founded it “for having materially assisted, sponsored, or provided financial, material, or technological support for, or goods or services to or in support of, the MOIS.”1 Ravin Academy and its founders have been known to the PwC Threat Intelligence team since early 2020 as having ties to several Iran-based threat actors including Yellow Nix (aka MuddyWater, MERCURY, TA450). We are publishing a portion of our private client reporting in light of the October 2022 indictments.
Who is Ravin Academy?
Ravin Academy is an Iranian company incorporated in 2019, that purports to provide cyber security education and training in both defensive and offensive fields. It also conducts vulnerability research, as well as specialized research into “advanced persistent (APT) teams.”2 PwC analysts identified the following incorporation records of Avayeh Hooshmand Ravin. We assess that this is the name that Ravin Academy was incorporated under.
| National ID |
14008970823 |
|
| Registration Number |
49135 | |
| Date Founded |
16th November 2019 |
|
| Address (Current) |
Second Floor, No. 36, Naqdi Street, North Sohrevardi Street, Shahid Ghandi-Niloufar Neighborhood, Tehran, Iran |
These incorporation records list the following corporate appointments. These match the co founders listed on Ravin Academy’s website and in the October 2022 US Treasury sanctions announcement.
| Name | National ID | Position |
| Seyed Mojtaba Mostafavi |
0080467741 | Chairman of the Board |
| Farzin Karimi Mazlganchai |
0440273961 |
Chairman of the Board of Directors |
Cofounder Conundrums
Both Ravin Academy co-founders have been accused, by various leaks, of being linked to the Iran-based threat actor we track as Yellow Nix, along with Yellow Maero (a.k.a. APT34)3, which we assess with high probability operates at the behest of Iran’s Ministry of Intelligence (MOIS).4 On 12th January 2022, US Cyber Command attributed Yellow Nix to a “subordinate element” within MOIS, which supports the claims made as a part of these leaks.5 Additionally, both of the co-founders who were named in the October 2022 indictment, as well as other Ravin Academy employees, were found to have personal associations with Iranian individuals we have previously linked to Iran-based threat actors. These links are as follows:
Seyed Mojtaba Mostafavi (a.k.a. Mojtaba Mostafavi) has previously been accused of working for Yellow Maero at the behest of MOIS by the “Lab Dookhtegan” leaks.6 This allegation was made in September 2019, two months prior to the formation of Ravin Academy in November 2019.
According to Mostafavi’s LinkedIn resume, he previously held the position of Chief Strategy Officer (CSO) at ArvanCloud between 2015 - 2019. ArvanCloud is an Iran based VPS and cloud provider known to PwC analysts as being associated with/used by multiple Iran-based threat actors. We have additionally observed multiple Iran-based threat actors, Yellow Nix, Yellow Liderc and Yellow Dev 19, use operational relay box (ORB) IPs assigned to ArvanCloud.7 ,8 ArvanCloud has also been linked to the Iranian Government through a public-private partnership to support Iran’s National Information Network (NIN) (a.k.a. Iran Cloud).9 Opponents of this project have raised concerns that it effectively isolates Iranian infrastructure, and can support the government’s ability to control and limit access in the future.10 We identified multiple documents in open source which list MOIS as an NIN stakeholder.11
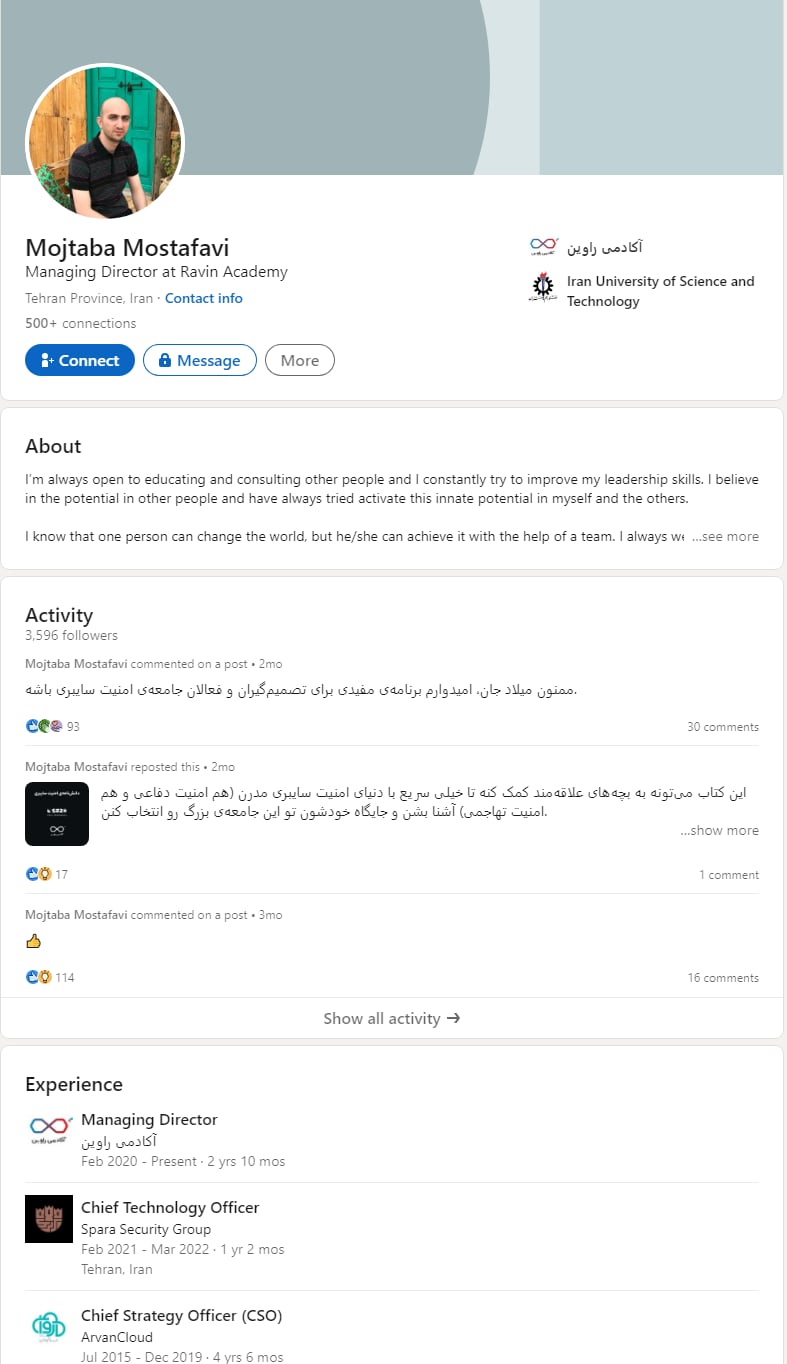
Figure 1 – Seyed Mojtaba Mostafavi’s LinkedIn profile
Farzin Karimi Mazlganchai (a.k.a. Farzin Karimi, Farzin Karimi Marzeghan Chai) is the second Ravin Academy co-founder. In 2019, a leak site named "Green Leakers” accused Farzin Karimi of being a leader of Yellow Nix operations.12 This allegation was made in April 2019, prior to the formation of Ravin Academy in November 2019. We consider some of the contents of the leak to be credible, specifically, a screenshot image of a purported Yellow Nix C2 panel showing IPs of current victims. At the time, the CEO of an Israeli security research company validated the Yellow Nix C2 panels as being legitimate.13 This suggests the "Green Leakers” operator was able to obtain access to infrastructure belonging to Yellow Nix and therefore it is possible that it was able to identify operators. Despite the inclusion of leak contents which are considered to be accurate, we are unable to confirm the allegation that Farzin Karimi is linked to Yellow Nix. PwC analysts are also aware of multiple instances where Farzin Karimi’s name and Twitter handle were embedded inside Yellow Nix samples. We assess that these samples were false flags, and were highly likely modified post-deployment in an attempt to link him to the threat actor.14

Figure 2 – Farzin Karimi’s LinkedIn profile
Ties to Yellow Nix
An examination of offensive cyber security training materials delivered by Ravin Academy show that it almost certainly has capability to both use and teach the same techniques Yellow Nix is known to use. These include persistence,15 DLL load order hijacking16 and exploitation. Additionally, PwC analysts have observed activity and tooling suggesting Yellow Nix operators may have been trained by Ravin Academy
Yellow Nix ZeroLogon exploitation
We identified a temporal overlap between Ravin Academy’s experimentation with CVE-2020- 1472 (a.k.a. ZeroLogon) exploitation, and Yellow Nix exploiting this CVE in attacks. This is shown in Figure 3.

Figure 3 – Timeframe showing Yellow Nix activity and Ravin Academy seminar17 18
On 5th October 2020, security researchers from Microsoft reported that Yellow Nix had exploited CVE-2020-1472 in multiple attacks since ~21st September 2020.19 The techniques Yellow Nix used in these attacks are outlined in Figure 4. On 23rd September, Ravin Academy delivered a webinar which demonstrated a proof of concept (POC) exploit for this vulnerability.
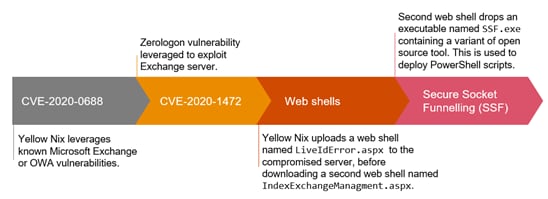
Figure 4 – Details of the Yellow Nix attacks observed by Microsoft, which use a combination of CVE-2020-0688 and CVE-2020-147220
We also identified a script that was uploaded to Ravin Academy’s public GitHub repository in March 2020.21 This script contains commands to exploit CVE-2020-0688, the same CVE and techniques leveraged by Yellow Nix in September - October 2020, as shown in Figure 5.
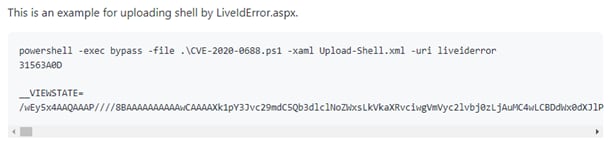
Figure 5 - Ravin Academy authored CVE-2020-0688 exploitation script, found on its GitHub repository22
The script contains example commands for uploading a webshell to a server post exploitation of CVE-2020-0688, with a webshell filename of “LiveIdError.aspx”. This is shown in Figure 15. This is the same filename as Yellow Nix’s webshells, shown in Figure 14. ClearSky researchers also observed Yellow Nix deploy a webshell with this filename in an attack in September 2020 alongside the exploitation of CVE-2020-0688.23 This does not appear to be a common filename, so one possible explanation for this overlap is that Yellow Nix used Ravin Academy’s materials.
Conclusion
Although we did not directly link the company to the threat actor directly, we assess that Yellow Nix is highly likely familiar with Ravin Academy’s training materials and it is possible the set is comprised of a prior student/s. It is common in Iran-based threat actor ecosystems for individuals to move between companies engaged in offensive operations. We have also previously identified Iranian individuals who have been linked to multiple distinct Iran-based threat actors believed to act at the behest of different Iranian government sponsors.24 The multitude of professional and personal links involving the Ravin Academy founders demonstrate the complexity of attributing Iran-based threat actor activity, as the lines are often blurred as individuals move around what has shown to be a small, intertwined ecosystem.
The outcome of sanctions and public disclosure of Iran-based operations has had mixed impact on the associated threat actors; specifically, some threat actors continue with their operations despite the disclosures, while others have ceased to operate. At the time of this publication, it remains to be seen how the October 2022 sanctions will impact the named entities and associated threat actor activity.
Footnotes
[1] https://home.treasury.gov/news/press-releases/jy1048
[2] CTO-SIB-20220121-01A - Advanced persistent teacher
[3] CTO-SIB-20200727-01A - Whos who of Iran-based threat actors
[4] Iranian intel cyber suite of malware uses open source tools’, US Cyber Command, https://www.cybercom.mil/Media/News/Article/2897570/iranian-intel-cyber-suite-of-malware-uses-open-source-tools (12th January 2022)
[5] ‘Iranian intel cyber suite of malware uses open source tools’, US Cyber Command, https://www.cybercom.mil/Media/News/Article/2897570/iranian-intel-cyber-suite-of-malware-uses-open-source-tools (12th January 2022)
[6] @lab_dookhtegan, Telegram, https://t.me/s/lab_dookhtegan (6th September 2019)
[7] CTO-TIB-20201118-02A - Learning on the job with Yellow Dev 19
[8] CTO-TIB-20200528-01A - Wading through smoke on the MuddyWater
[9] “Riding the Clouds”: Abr Arvan Cloud Company and the Perspective of Internet Restriction in Iran, Zamaneh Media, https://en.radiozamaneh.com/31799 (29th August 2021)
[10] CTO-GCB-20210412-01A - Global Cyber Bulletin - March 2021
[11] ‘National Information Network National Plan and Architecture’(Translated from Farsi), RRK, 7th October 2020
[12] CTO-TIB-20200514-02A - A muddy masquerade
[13] Omri Segev Moyal, @GelosSnake, Twitter, https://mobile.twitter.com/GelosSnake/status/1124386041736105984 (3rd May 2019)
[14] CTO-TIB-20200514-02A - A muddy masquerade
[15] ravinacademy, Aparat, https://www.aparat.com/RavinAcademy
[16] ‘Iranian intel cyber suite of malware uses open source tools’, US Cyber Command, https://www.cybercom.mil/Media/News/Article/2897570/iranian-intel-cyber-suite-of-malware-uses-open-source-tools (12th January 2022)
[17] CTO-SIB-20220121-01A - Advanced persistent teacher?
[18] ‘Operation Quicksand’, ClearSky, 2020, https://www.clearskysec.com/wp-content/uploads/2020/10/Operation-Quicksand.pdf
[19] ‘Operation Quicksand’, ClearSky, 2020, https://www.clearskysec.com/wp-content/uploads/2020/10/Operation-Quicksand.pdf
[20] CTO-TIB-20201020-01A - Seedworm sees a CVE
[21] https://github.com/ravinacademy/CVE-2020-0688
[22] ‘CVE-2020-0688’, Ravinacademy, GitHub, https://github.com/ravinacademy/CVE-2020-0688 (31st March 2021)
[23] ‘Operation Quicksand’, ClearSky, https://www.clearskysec.com/wp-content/uploads/2020/10/Operation-Quicksand.pdf
[24] CTO-SIB-20200727-01A - Whos who of Iran-based threat actors
Contact us

Cyber Threat Operations Lead Partner, PwC United Kingdom
Tel: +44 (0)7725 707360













