{{item.title}}
{{item.text}}

{{item.text}}
In 2016 attackers compromised systems at the Bangladesh Central Bank and sent payment instructions totalling USD $951m, of which $101m were processed by the Federal Reserve Bank of New York. This remains the biggest bank heist in history.
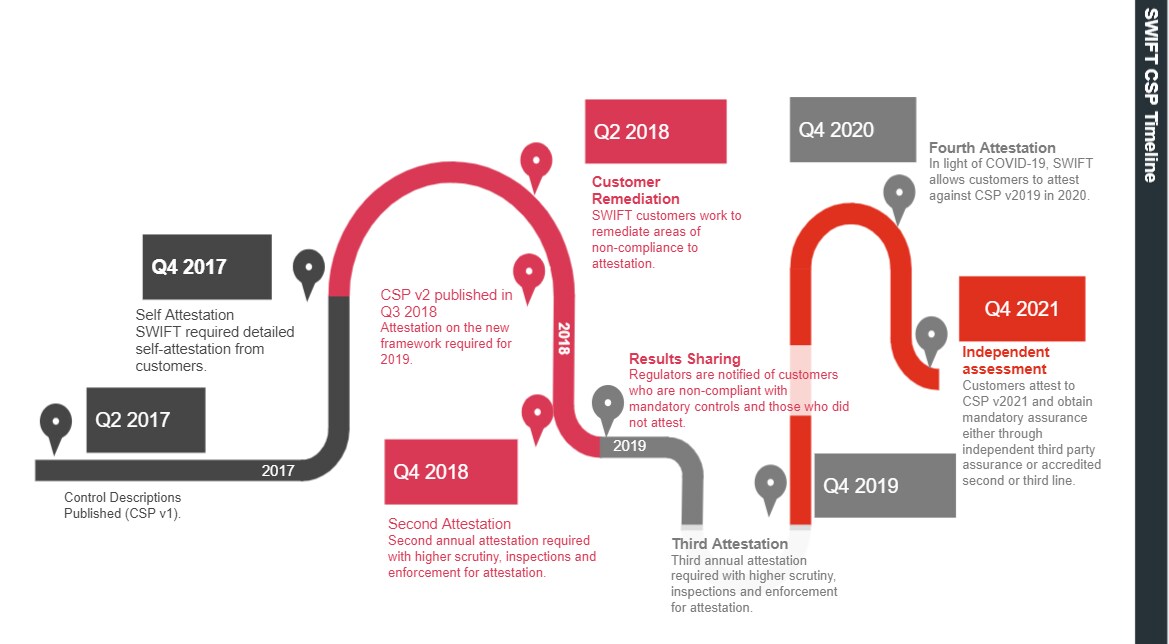
Since this time, SWIFT's payments community continues to suffer from a number of cyber-attacks and breaches. While all SWIFT customers remain primarily responsible for protecting their own environments, SWIFT aims to support its community in the fight against cyber-attacks. In 2017, SWIFT published its Customer Security Programme which consisted of 16 mandatory and 11 advisory (optional) security controls which they required their 11,000 customers worldwide to self-attest to on an annual basis.
This has evolved over the years and has now been refined to 22 mandatory and 9 advisory (optional) security controls as per the latest SWIFT Customer Security Controls Framework (“CSCF”) v2021, which was released in July 2020. Furthermore, for 2021, SWIFT has introduced a requirement that mandates an independent assessment for all customers' attestations to be performed either through use of an independent third-party or accredited second line (e.g Compliance) or third line of defense (e.g Internal Audit). This was originally planned to be implemented in 2020, but was delayed due to the COVID-19 pandemic.
The latest SWIFT CSCF v2021 builds incrementally on v2020 and therefore adds to it. Minimal changes were made to ensure that customers have sufficient time to fully implement controls from previous CSCF versions. A brief summary of changes are as follows:
Note: As a result of the global COVID-19 pandemic, SWIFT published updated guidelines on 18 June 2020 regarding changes to the CSP self-attestation and independent assessment requirements for 2020 and announced that in 2020, customers had the option to self-attest against the 2019 version of the SWIFT CSP and optionally support the self-attestation with an independent assessment. In 2021, an independent assessment will be a mandatory requirement and customers will be required to attest against the 2021 version of the CSP framework.
PwC will leverage inhouse accelerators and our extensive SWIFT CSP expertise to ensure that your needs are met ahead of SWIFT's required independent assessment due on 31 December 2021.
We have performed numerous SWIFT CSP assurance engagements across multiple territories and industries.
We understand SWIFT like no other as we performed an annual review of SWIFT under the internationally recognised ISAE3000 standard for over 10 years.
We are the only ‘Big-4’ firm with a professional Certified Cyber Security Consultancy certificate from the NCSC. We are unique in our ability to leverage threat intelligence to build and simulate realistic cyber-attack scenarios.
PwC will leverage inhouse accelerators and our extensive SWIFT CSP expertise to ensure that your needs are met ahead of SWIFT's required independent assessment due on 31 December 2021.
PwC will provide industry insight that is relevant to your market segment and geographical segment, as well as a balanced view on how to prioritise any associated actions.
SWIFT's customer security programme (CSP) aims to prevent and detect fraudulent activity through a set of mandatory security controls, community-wide information sharing initiatives and enhanced security features on their products.
SWIFT's customers are required to submit their attestations on an annual basis to SWIFT's KYC portal by 31st December.
In 2020, customers were able to self-attest their compliance to either CSCF v2019 or CSCF v2020. In 2021, an independent assessment is required, alongside the customer's attestation, to CSCF v2021.
There are two forms in which a SWIFT customer can gain an independent assessment:
There are 22 mandatory controls focussed on 3 key objectives: securing your environment, limiting access, detecting and responding. These key objectives span the following 8 principles:
SWIFT reports all cases of non-compliance and where members have not attested at all to local regulators. In addition SWIFT will select a sample of attestations for validation each year.
It is vital that you share all relevant information and let SWIFT know there is a problem as soon as possible, in order to protect other organisations in the network.
{{item.text}}

{{item.text}}