
Every new convenience adds risk
The automotive industry is facing an inflection point: As internet connectivity becomes commonplace, it increases the risk that privacy – and even safety – will be compromised.
In 2015, we got a glimpse at what is at stake, when two security researchers hijacked a vehicle over the internet. They were able to turn the steering wheel, briefly disable the brakes, and shut off the engine. The implications of this exercise were clear and troubling at the time. Now with many more cars internet-enabled, the risk of hijacking has exploded. And the trend will continue unabated because consumers want the convenience of connectivity. However, every new convenience adds risk, and current security protections generally fall short of countering that risk.
Cyber risks to the enterprise
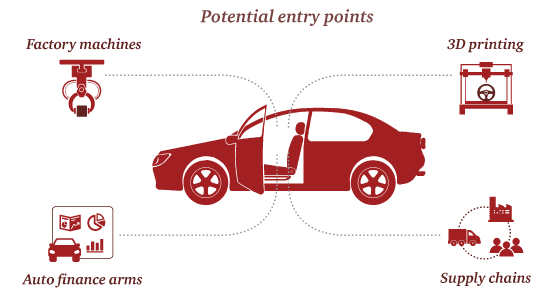
Car safety has to be supported by an enterprise-wide program that coordinates cyber defenses across all production platforms, internal operations, and supply chains. A weakness in one area can infect the rest of the enterprise and result in, for example, car failure, factory slowdowns, the hacking of customer data, or the theft of intellectual property. There are several obvious entry points for intruders, including factory machines, 3D printing, auto finance arms, and supply chains.
Holistic, layered approach to cybersecurity
Cyber resilient companies develop a holistic approach to fighting cyberattacks that includes prevention, detection, and reaction as well as a feedback mechanism. Following are some of the industry’s best practices for securing the enterprise against cyber threats:
- Get buy-in at the highest levels to build a security culture
- Prioritize assets and threats
- Define and integrate processes
- Follow cybersecurity core team best practices
- Address supply chain risks
- Invest in advanced tools and technology
Get buy-in at the highest levels to build a security culture
As with any other critical risk, C-level executives and the board of directors need to be engaged in budgeting for security and fostering a security culture throughout the organization. All employees have to share in security awareness and understand their roles and responsibilities in preventing cyberattacks. Any part of the organization can become a victim of intrusion, and a failure in one area can affect the others. Security policy and heightened awareness of cyber risk have to be woven into the fabric of the culture through tone at the top, education, and HR policies.
Prioritize assets and threats
Since it’s too expensive to protect all assets, automotive companies should determine which are their most valuable and focus aggressively on protecting them. Companies also need to categorize and prioritize the kinds of threats they are facing, now and in the next few years, as well as the perpetrators most likely to do damage. Some companies use threat intelligence services to help keep track of the latest industry threats, which are then fed back into security operations procedures.
Define and integrate processes
Clearly defined processes help to reduce the time from incident to detection to response. They should include a matrix that places attacks on a graduated scale of potential impact based on degree of financial/operational/brand exposure, number and type of systems compromised, and a clear plan for notifying internal and external stakeholders. They should also contain sensitivity and analytical capability that can discern false positives driven by external or internal events that are unrelated to an intrusion.
Follow cybersecurity core team best practices
A best practice is to form a working group with permanent representatives from three critical groups—information or cyber security, legal, and corporate communications—that are responsible for dealing with incidents. Within this group, there should be a single leader who serves as response coordinator and is recognized as such by the entire group so there is no confusion, delay, or disconnected communications among team members.
Address supply chain risks
Automotive companies need to monitor their partners’ operations for potential security breaches and manage the access of users to different systems. Smaller vendors present special risks, since they tend to have less stringent security protocols, so contracts should include audit clauses and mandated testing procedures.
Invest in advanced tools and technology
State-of-the-art technology is needed to fight back against increasingly sophisticated threat actors and vectors as well as to mitigate the risk of valuable corporate data dispersion throughout organizations and supply chains. One way to stay current is to leverage the capabilities and infrastructure of subscription-based services that use the cloud. These services provide real-time updates that aggregate information and keep defenses fresh and dynamic. But it is equally important to deploy and configure tools that meet each organization’s specific operating circumstances.









