Are you earning trust with stakeholders? Put your data protection program to the test
05/06/22
Consumers and employees agree: Data protection and cybersecurity are the top components of business trust, as revealed in PwC’s 2024 Trust Survey. We’ve put together a six-step approach to help you operationalize your privacy and data protection programs.
Complicating matters is the fact that your data protection, privacy, compliance and cybersecurity programs are subject to regulatory scrutiny. How can you be sure that your practices are meeting the expectations of all relevant stakeholders?
A closer look
There is some good news. The steps you take to satisfy regulators are the same moves that will help you build strategic advantage at a time when companies are increasingly competing on trust. We suggest building your plan on what we’ve learned from helping assess programs, recommending actions and assisting in remediation and post-enforcement actions for a range of companies.
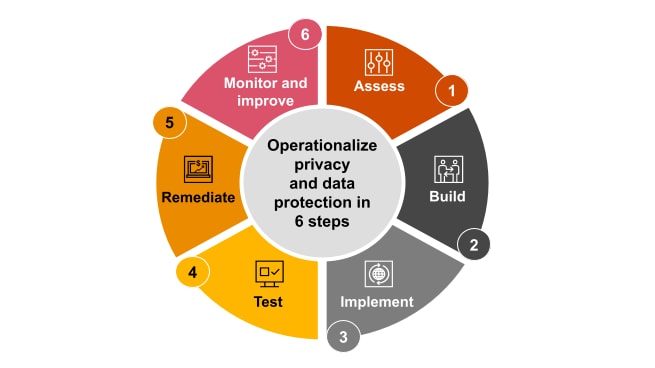
1. Assess the current state.
First, gain an in-depth, up-to-date understanding of the current state of your data, your regulatory environment, your privacy and data protection controls and your systems and business processes. Next, dig into your data privacy and protection environment by performing a risk-based gap assessment of your systems, applications, controls and data.
2. Build on a foundation using recognized frameworks.
When designing or enhancing a privacy and data protection program, start with a trusted framework to help guide your approach. Some of the go-to standards that cover the essentials while allowing for individual flexibility include:
- National Institutes of Standards and Technology (NIST) Cybersecurity Framework.
- NIST Privacy Framework.
- International Organization for Standardization (ISO) 27001 for information security management.
- ISO 27701 for data privacy controls.
The appropriate framework will help you outline policies, procedures, standards and controls. You’ll also want a plan to measure key performance and risk indicators in your processes for regularly reporting to management and the board.
3. Implement the program with control operators and owners.
Senior level executives should be appointed as control owners who will be accountable for the consistent and effective design and ongoing review and segregation of duties needed for the operation of your program controls. Control operators are individuals who report to control owners and are responsible, on a daily basis, for executing the controls. Separating these responsibilities is a hallmark of creating strong controls.
4. Test the program.
Leading practice dictates that the program is evaluated and tested in three ways. The control operators and owners evaluate the program daily by determining whether the controls are operating effectively. Then, there should be a group in the “second line of defense” that monitors the program. This monitoring could be through metrics with established thresholds or through sample testing of controls. And finally, internal audit should periodically examine the controls that comprise the program both for design and for operating effectiveness. We recommend applying the same rigor in your own testing that you would face in the event of an enforcement action.
5. Remediate any performance gaps identified in testing.
Once you have a clear handle on which controls operate effectively and which need enhancement, remediation can begin. Leading practice is to document these issues and address them both strategically and tactically until each one is remediated. Consider automation and efficiency when possible.
6. Continuously monitor and improve.
Implementing a privacy and data protection program is never a one-time undertaking. Businesses evolve. Systems are regularly upgraded or expanded as new threats emerge and regulations change. You’ll want a plan and the resources to sustain a repeatable process.
Worried about covering all of the bases? PwC can help with a comprehensive review of your entire data protection program or target our assistance with any of the specific steps. Our professionals have experience helping companies in a range of industries at every step of the data protection journey. PwC can provide insight to how other organizations have addressed similar issues as well as how to remediate controls so they will withstand regulatory scrutiny.
Enforcement orders require an experienced and pragmatic response
In today’s business world, regulators are watching and, in some cases, their questions lead to investigations and consent orders. Responding to inquiries or enforcement orders from a regulator can be daunting and require experience and knowledge of complex processes and requirements.
The urgency of complying with a consent order leaves no room for error or delay. PwC has significant experience with building and assessing privacy and data protection programs in response to consent orders. Our approach is proactive and pragmatic, and we coordinate all relevant stakeholders so that the program is enhanced effectively and efficiently.
Click here to initiate a discussion of your existing data-protection practices, potential points of vulnerability and ideas for improvement.
Contact us











