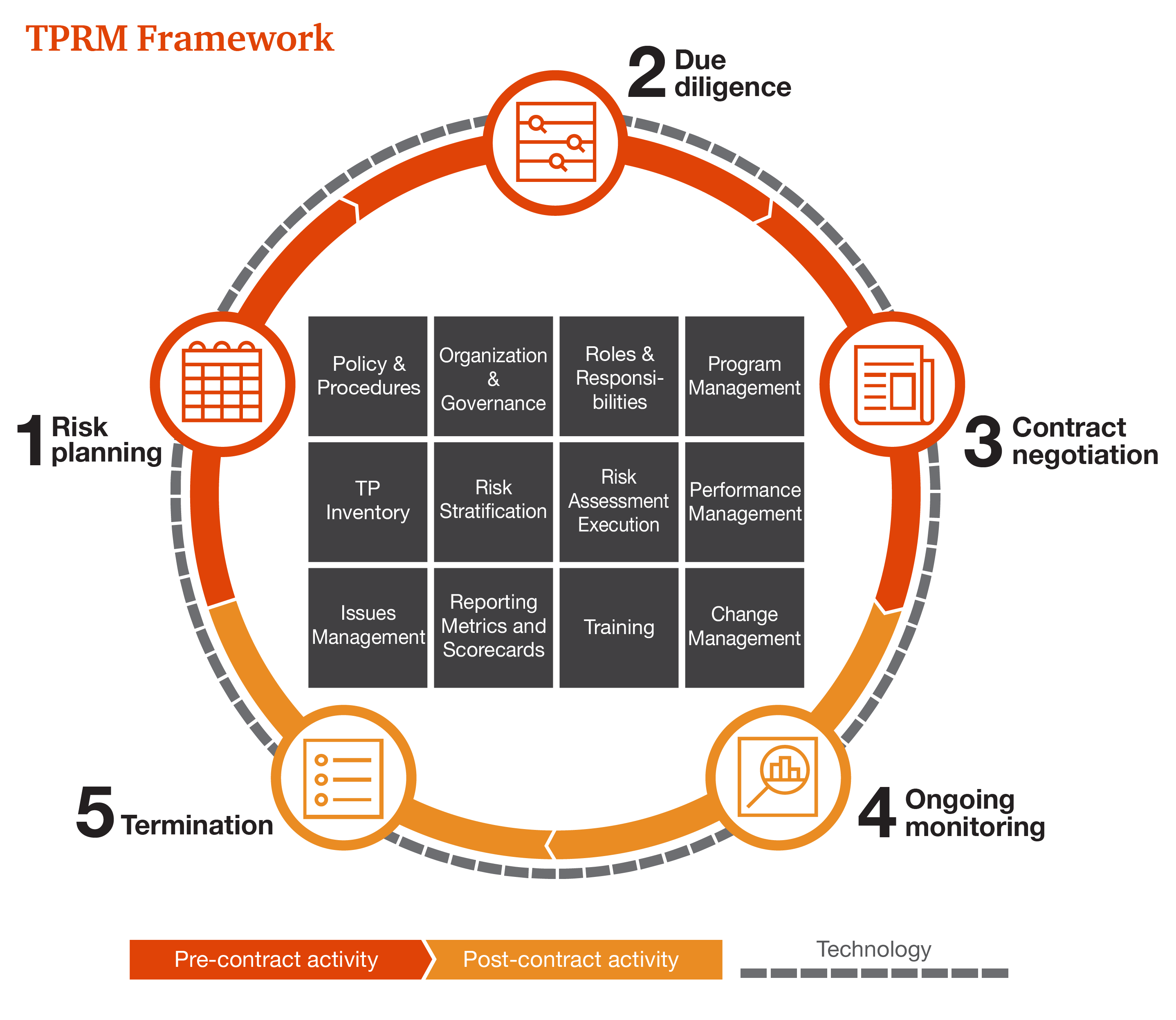
{{item.title}}
{{item.text}}

{{item.text}}
Our team applies innovative approaches and technologies that help our clients effectively manage their risk exposure so they can properly identify, mitigate and monitor the third-party risks most impactful to their operations. We help our clients design, build and manage fit-for-purpose third-party risk programs that protect their operations, brand and reputation at an optimal cost to operations.
TPRM Program Assessment:
Compare your program maturity against industry peers, regulatory expectations and leading practices to enhance your TPRM program commensurate with the risks posed by your network of third parties
Program Design & Build:
Design and build a fit-for-purpose TPRM program that protects your organization's operations, brand and market reputation
TPRM Assessment Support:
Conduct high-volume third-party risk assessments targeted to specific risk areas. Define and assess the proper third-party controls through observations, review of requested evidence as well as remote and on-site verification testing
Technology Selection, Implementation & Optimization:
Select the most appropriate TPRM technology solutions to meet your third-party risk management needs. Review and optimize existing TPRM applications to improve technology coverage and drive a consistent, efficient and integrated TPRM program
TPRM Managed Services:
Receive end-to-end TPRM technology and process support that meets the needs of your operations, risk profile and regulatory expectations
Customer Risk Response:
Organize, structure, and build a formal, technology-enabled program to streamline the management of customer audit and risk assessment requests, based on a library of standardized, approved responses
{{item.text}}

{{item.text}}