Balance security, privacy and opportunity to move boldly forward
Cyber Security

We don’t just protect business value, we create it — using cyber security and privacy as a tool to build trust in a digital, data-driven world.
As companies pivot toward a digital business model, exponentially more data is generated and shared among organizations, partners and customers. This digital information has become the lifeblood of today’s interconnected business ecosystem and is increasingly valuable to organizations—and to skilled threat actors. Business digitization also has exposed companies to new digital vulnerabilities, making effective cyber security and privacy more important than ever. PwC can help you take a broader view of cyber security and privacy as both protectors and enablers of the business.

Our goal is to help improve the knowledge, skills, competence and expertise of professionals in the areas of information/cyber security, privacy, IT standards and information/cyber security governance, risk and compliance. This will in turn help organisations meet the challenges arising in the rapidly evolving cyber security space as well as help build relevant capabilities and functions.
Cyber Arena
Forget boring cyber security trainings and endless presentations. With Cyber Arena, you will gain practical experience. A unique simulation of risk assurance and defence strategy will offer a clearer understanding to the members of your management and technical team. You will learn to act fast when in a crisis and to efficiently build a modern and safe company.
In today's ever-evolving cyber threat landscape, organizations need a robust defense strategy to protect their valuable data and assets. Blue teams play a crucial role in this defense by proactively identifying, analyzing, and responding to cyber threats.
Our technical consultancy team offer a wide range of services to help your organization stay ahead of cyber threats, including:
Penetration testing: Blue teams can perform penetration testing based on black box, white box, and grey box methodologies. These approaches help evaluate the organization’s security posture, identify weakness and recommend mitigations to strengthen defenses against potential attacks.
Cyber threat hunting/ Threat Intelligence: Blue teams apply a proactive approach to identifying and analyzing previously unknown, or ongoing non-remediated cyber threats.
Social Engineering: Blue teams develop and conduct educational programs to improve cyber security hygiene among employees and reduce social engineering risks such as phishing, watering hole attacks, vishing, whaling , hoaxes , etc.
Incident response: In the event of a cyberattack, blue teams can quickly and effectively contain the incident, minimize damage, and restore normal operations.
Security awareness training: Blue teams can help educate your employees about cyber security threats and best practices to reduce the risk of human error.
SOC set-up: Blue teams can assist in setting up and managing a Security Operation Center (SOC) to centralize your organization's security monitoring and incident response capabilities.
The aim of red teaming is to replicate the techniques used by real world attackers by delivering bespoke intelligence driven simulated attack exercises that assess the full suite of defence in depth controls, including the often overlooked areas of people and processes. Our red team helps organisations understand how they can defend themselves against a cyber attack with a particular goal in mind, such as gaining access to a critical application, stealing privileged information or investigating susceptibility to ransomware. We further focus our approach based on the risk profile for each client to make our ethical hacking services as realistic and tailored as possible.
Our security testing services include but not limited:
Application Security Testing: We rigorously test your application or infrastructure for vulnerabilities like injection flaws, broken authentication, and insecure configurations.
Security Code Review: Our meticulous code review process identifies potential security weaknesses, coding errors, and design flaws that could be leveraged by attackers.
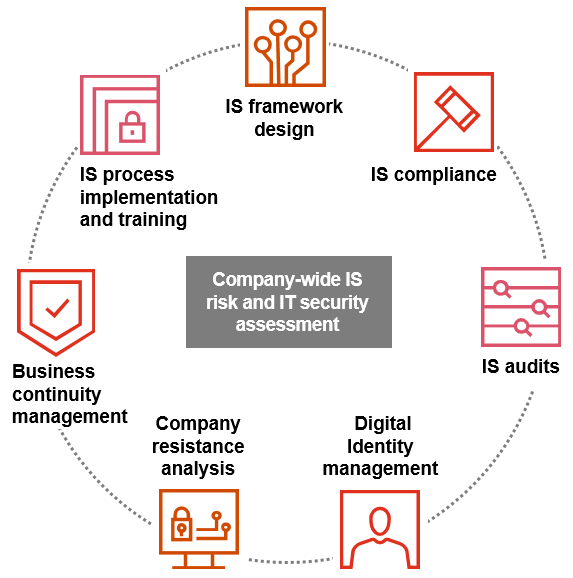
Our service includes a detailed current status analysis by thoroughly examining your existing procedures and policies. Our evaluation covers all aspects of your cyber security framework, identifying strengths and areas for improvement. This analysis is conducted using best practices and recognized standards such as NIST (National Institute of Standards and Technology) and ISO 27001, ensuring that our recommendations are aligned with industry-leading benchmarks.
Our goal is to give you a clear understanding of your cyber security posture and offer tailored recommendations that address your unique needs. This approach not only helps you strengthen your security framework but also ensures compliance with regulatory requirements and best practices.