We will protect your data and technology by ensuring the cybersecurity of your information systems
CyberSecurity 2.0

Business digitalisation creates new jobs, boosts competitiveness and promotes development, while also creating new challenges in terms of cybersecurity and data security.
Cybersecurity 2.0 is not only based on the principles of protection, detection and response used earlier but it includes three new principles: promptness, complication, and anticipation:
- Promptness is a fast response to various threats and vulnerabilities in IT systems to detect and eliminate them within as short a time frame as possible.
- Complication is making penetration opportunities complicated for attackers so they have difficulty in accessing, finding and stealing sensitive data even if they infiltrate the network.
- Anticipation is the ability to monitor the entire IT infrastructure, identify new unknown threats and zero-day attacks by summarising and analysing internal and external threat information, as well as constantly checking and improving the IT protection systems and their responsible experts.
PwC cybersecurity
Cybersecurity services
- Cybersecurity transformation
- Monitoring and analytics services
- Pentest
- Source code analysis
- Evaluating and devising a cybercrisis plan
Cybersecurity transformation
Cybersecurity transformation services help organisations develop and transform from a reactive to a proactive and adaptive cybersecurity practice for a single corporate protection strategy.
To keep up with the fast growing cybersecurity threat environment, companies need knowledge, understanding, strategic planning, and teamwork. Our experts have comprehensive technical knowledge and experience as well as an understanding of business risks. We will help you devise a new cybersecurity strategy or improve your existing one to ensure it actively protects your company against today’s cyberthreats.
Develop your cybersecurity through PwC services:
- Creating a cybersecurity strategy and a roadmap
- Redesigning the organisation of cybersecurity
- Rationalising your cybersecurity portfolio and investment
- Cybersecurity architecture and operations
- Wide-ranging implementation of cybersecurity monitoring technology
- Educating the board and managers
- Staff cybersecurity training
- Social engineering simulations
- Customer data protection, experience and trust
- Third-party IT services security and risk analysis
- Your digital identity and potential incident risks.
Monitoring and analytics services
To improve their competitive edge, companies need to improve their security measures – make the best use of new technology and quickly respond to threats when they arise, or best of all, before they arise (proactively). To improve their cybersecurity, many companies begin implementing LM/SEM/SIEM (Log Management/Security Event Management/ Security Information and Event Management) technology for IT event auditing, analysis and storage, as well as creating their own security operation centres (SOC) using a combination of technology, processes and trained employees to monitor security incidents and respond appropriately and quickly. All these systems are complex and very expensive, which makes their selection and implementation a complicated and time-consuming process that does not always guarantee a successful outcome.
PwC ITS experts have vast experience in creating and developing advanced monitoring and analytics centres as well as security management centres (SOC) in customer infrastructures. In this area we help our customers with these services:
- Conducting a financial assessment and preparing your business for setting up SIEM/SOC
- Creating your SIEM/SOC strategy and budget
- Comparing various SIEM/SOC implementation options either in your company or as a service (MSSP)
- Evaluating SIEM/SOC technology, processes and staff, using PwC’s patented SOCCER methodology
- Devising a stable SIEM/SOC organisational structure
- Auditing the functions and quality of your existing SIEM/SOC system
- Implementing SIEM/SOC metrics and KPI and visualising management and technical staff reports
- Running a health check to assess the performance of technologies used
- Creating high-level target technical architecture for SIEM/SOC information security tools
- Drawing up recommendations for implementing application cases for risks and threats facing your company
- Developing and implementing key SIEM/SOC processes
- Describing staff roles and responsibilities as well as skills required for performing various functions.
Pentest
Cybercriminals are rapidly evolving and using increasingly newer and more efficient technologies (ML and AI) in creating threats. Hackers can be outside or inside your company (often employed by it for years). It may well be that your information resources are tested and hacked, as autonomous viruses can carry out such unauthorised actions constantly. How cybersecure is your IT infrastructure? How can you proactively identify potential threats before they materialise? How can you avoid losing reputation in the eyes of customers? PwC ITS pentest team can help answer all these questions.
We test the cybersecurity of infrastructure and apps with a focus on identifying and exploiting vulnerabilities inherent in business critical IT infrastructure and apps (internal and external):
- Comprehensive infrastructure pentest
- Security checks of Web, Cloud, Mobile and other external resources
- Pentest using Black, White or Grey Box principles
- Drawing up recommendations to mitigate known security vulnerabilities
- Cybersecurity team’s response efficiency assessment
- Source code analysis (dynamic or static)
- Your digital identity threat assessment (OSINT).
Source code analysis
According to market researchers, 90% of vulnerabilities exist in app source codes deeply buried in the developers’ workstations and not accessible to most security tools and tests.
Unfortunately most companies do not subject their app source codes to security checks and analysis, which causes dangerous security gaps in the stages between the new app development stage and their full-fledged launch in a production environment.
PwC ITS cybersecurity experts will carry out an in-depth analysis of your app codes to detect security vulnerabilities in:
- Input validation logic
- Memory management
- Authentication
- API integrity and applicability etc.
Evaluating and devising a cybercrisis plan
Many companies and government agencies are facing increasingly advanced and harmful cyberattacks whose scale and complexity have grown dramatically in recent years. Their financial, operational and reputational impact can be immediate and can create long-term challenges to your development. That is why it is important for companies to understand what cybersecurity threats they face, how to respond to them and whether your company is prepared for a cybercrisis, given the new data security rules (e.g. GDPR) and digital transformation challenges in corporate development.
PwC’s cybersecurity crisis plan assessment and development service will help you escape from situations where your company detects a cyberincident or a data breach. The service provides a strategic framework and runs activities to ensure you are prepared for a cyberincident, know how to respond to it and begin coordinating recovery after the incident. The plan:
- includes modelling various types of cybercrisis situations;
- identifies potential goals and their impact on your ICT;
- defines the actions and responsibilities of the persons in charge (within your company and between related cybersecurity service providers or government security units and their agencies).
To ensure that your plan for overcoming cybersecurity crises is effective when a crisis sets in, the plan needs regular updates and checks. Keeping your plan in working condition is a continuous process in your company. PwC’s team of cyberexperts will ensure your readiness for a cybercrisis.
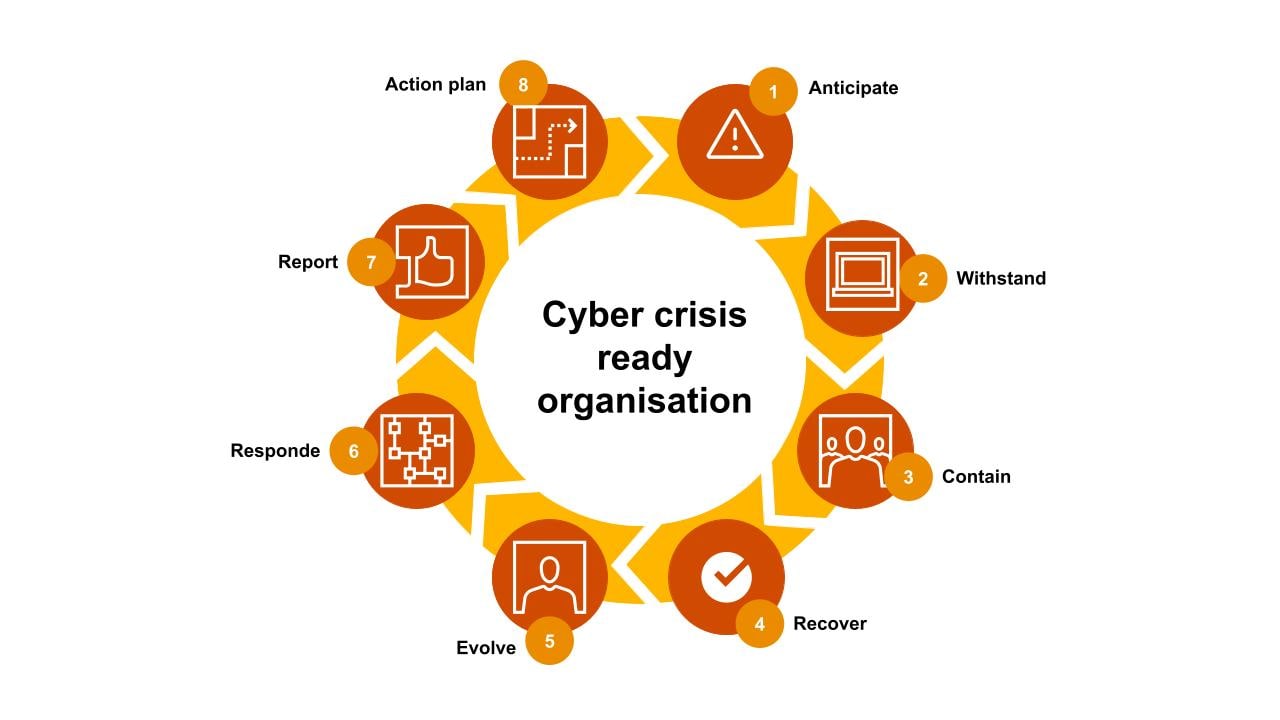
A company prepared for cybersecurity crisis is defined by the conditions below:
- Existing and new threats and risks are proactively identified, mitigated and monitored.
- Crisis tools and technologies have been implemented and are understood.
- Crisis management promotes an organisational culture that allows you to act and make fast decisions during a crisis.
- Crisis management promotes continuous improvement of crisis capabilities to avoid new risks.
- Crisis management and the persons in charge are regularly trained to solve crisis situations.
- Internal crisis options, vulnerabilities and weaknesses are understood and prevented.
- Roles and responsibilities are arranged and understood among your employees.
- Your cybercrisis response process and priorities are clearly defined.
Contact us







