
The 2022 Global Digital Trust Insights survey of 3,602 business and IT executives, including respondents from across the Middle East, looks at the current cyber landscape and what challenges and opportunities organisations face to simplify and improve their cybersecurity going forward.
Investments are continuing to pour into cybersecurity. Fifty-eight percent of Middle East organisations predict a rise in cyber spending in 2022 compared to 43% last year. More than a third (31%) predict cyber spending hikes of 10% or more; only 10% percent said that last year. Organisations know that risks are increasing with more than 43% expect a surge in reportable incidents next year above 2021 levels.
Already, 2021 is shaping up to be one of the worst on record for cybersecurity. Ever more sophisticated attackers are plumbing the dark corners of our systems and networks, seeking — and finding — vulnerabilities. Whatever the nature of an organisation’s digital Achilles’ heel — an unprotected server containing 50 million records, for example, or a flaw in the code controlling access to crypto wallets — attackers will use every means at their disposal, traditional as well as ultra-sophisticated, to exploit it.
The consequences for an attack rise as our systems’ interdependencies grow more and more complex. Critical infrastructures are especially vulnerable. And yet, many of the breaches we’re seeing are still preventable with sound cyber practices and strong controls.
Key findings and takeaways
Be deliberate about simplicity and simplification
In an overly complex organisation, it’s easy for the left hand not to know what the right hand is doing — and the consequences for cybersecurity and privacy can be dire. More than 65% of the Middle East respondents say their businesses are too complex, avoidably and unnecessarily so, and nearly as many say complexity poses “concerning” cyber and privacy risks to their organisations especially when it comes to governance of data, data infrastructure and technology applications.
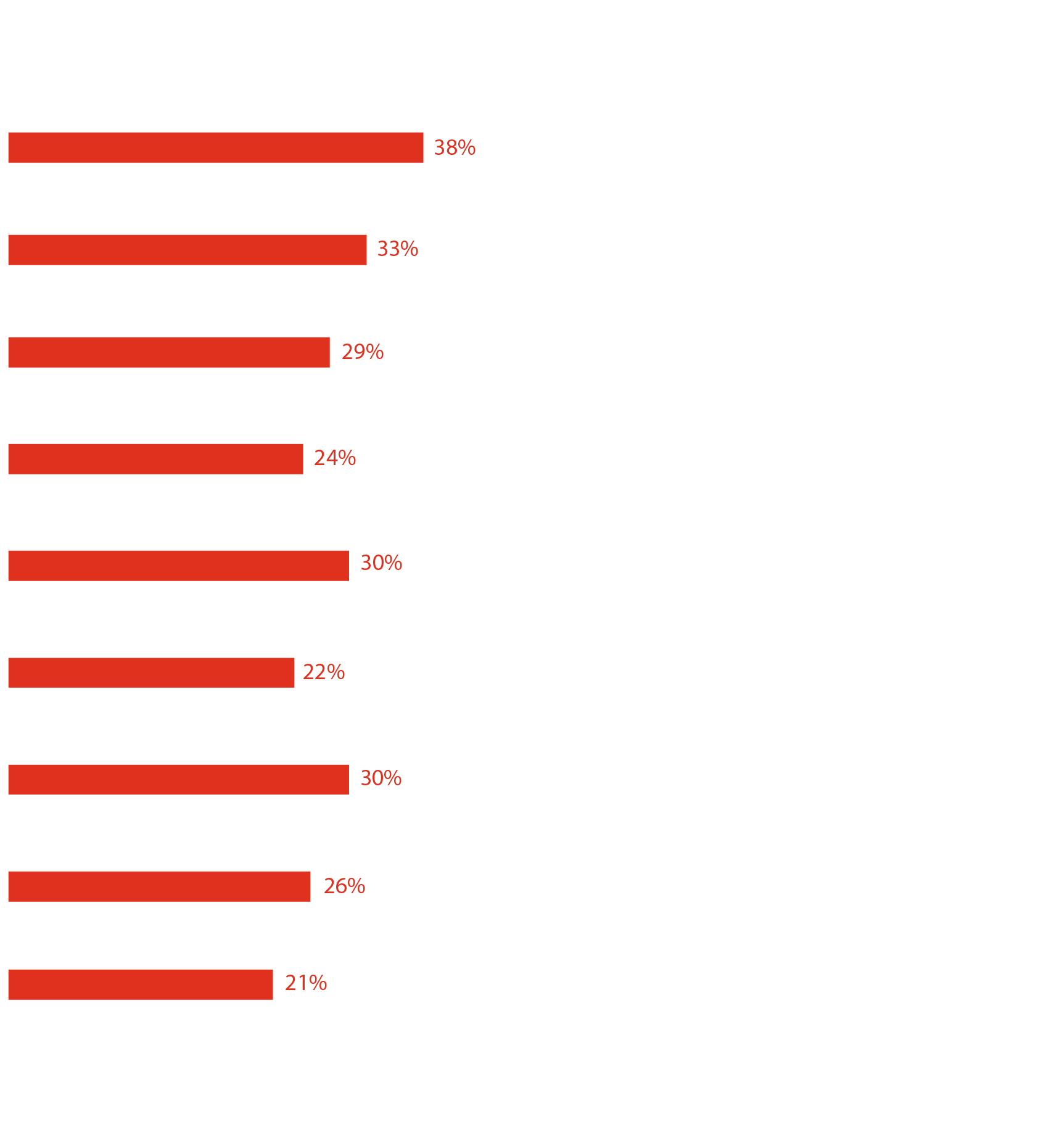
Asked to name the top consequences of operational complexity, our Middle East respondents identified:
Inability to innovate as quickly as the market opportunities offer
Lack of operational resilience or inability to recover from a cyber attack or technology failure
Financial losses due to successful data breaches or cyber attacks.

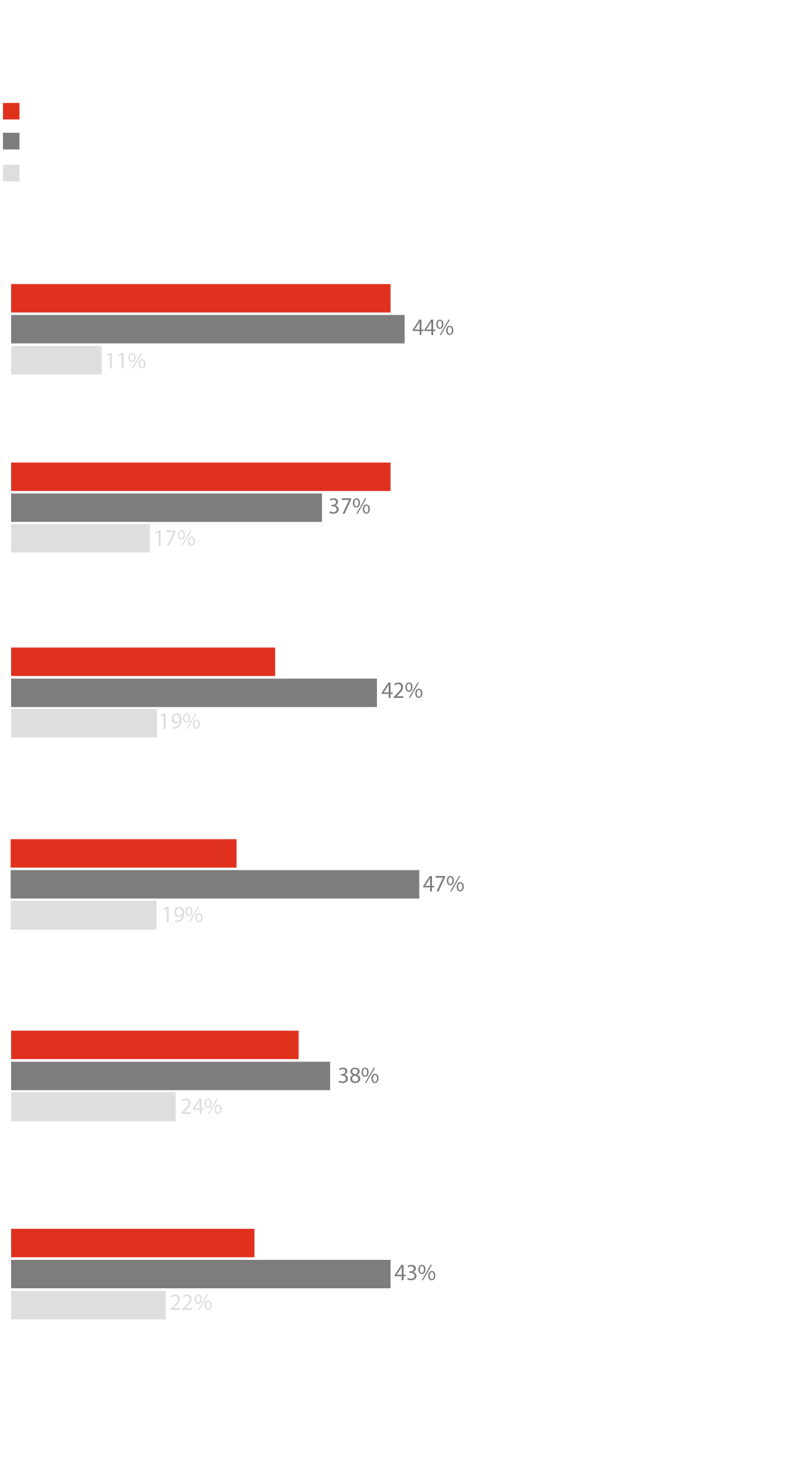
Businesses are aware of the risks of complexity, and around a third of our respondents have completed enterprise wide streamlining of their operations. However there are still some who are playing catch up with a quarter saying they’ve done nothing at all or are just getting started. But a shift appears to be underway.
To be fair, simplifying cybersecurity can be challenging. Even knowing where to begin can be difficult, especially given the attacks hitting businesses on every front. Asked to prioritise among nine initiatives aimed at simplifying cyber programs and processes, respondents couldn’t choose, allotting near-equal importance to all of them.
Simplifying an organisation takes time, requiring changes in viewpoints and company culture. That’s not easy to achieve, but the payoffs are mighty.
Size up your risks — using data you can trust — to realise opportunities
Data is the asset attackers covet most but companies can minimise that risk by minimising the target. But only 33% of respondents have mapped all their data, meaning they know where it comes from and where it goes. And only about a third report having mature, fully implemented data-trust processes. Organisations should govern, discover, and protect only the data they need — and eliminate the rest. Low-value data not only creates unnecessary risk, it also crowds out or buries high-value data.
Effective data governance is important not only for operational resilience but also for compliance with regulations. Some Middle Eastern countries already have data privacy regulations in place and more are likely to follow. When someone asks for information about their data — what you’re keeping and what you’re doing with it — you’d better be able to answer quickly and accurately. If it’s a regulator doing the asking, the wrong answer could bring heavy fines depending on the jurisdiction.
Utilising the data you have to make informed decisions, can unlock significant benefits, however chances are high that neither you nor your competitors are letting data inform your cyber risk management. Fewer than one in three of survey respondents say they’ve integrated analytics and business intelligence tools into their operating model. These respondents scored lowest in their ability to turn data into insights for cyber risk quantification, threat modeling, scenario building and predictive analysis — all critical technologies for smart cybersecurity decisions.


New types of internal data, data from new external sources, new data partnerships and information-sharing platforms can be important sources of business intelligence, but only about a quarter of respondents say they’re reaping benefits from these tools.
Businesses predicting an increase next year in their cybersecurity spending are often the same enterprises whose operational models use business intelligence and data analytics. Data can not only help you spend your cyber budget wisely, it can also help you get more to work with.
Shrink the large blind spot hiding the risks in your business relationships
You can’t secure what you can’t see, and most respondents in our 2022 Digital Trust Insights Survey seem to have trouble seeing their third-party risks — risks obscured by the complexities of their business partnerships and vendor/supplier networks.
An organisation could be vulnerable to a supply chain attack even when its own cyber defences are good, with attackers simply finding new pathways into the organisation through its suppliers. Detecting and stopping a software-based attack can be very difficult, and complex to unravel. That’s because every component of any given software depends on other components such as code libraries, packages and modules that integrate into the software and are necessary for its operation.
Gaining visibility into the web of third-party relationships and dependencies is a must. Top cybersecurity companies integrate solutions (real-time threat intelligence, threat hunting, security analytics, vulnerability management, intrusion detection and response) on broad platforms.
Contact us








